The blog describes some troubleshooting steps you can take if you have followed the process to on-board Windows 10 to WDATP (as described here), but the devices are not appearing in the Machine List on Windows Defender ATP portal
- From the Windows 10 device, verify the diagnostic data service is enabled and running
Open an elevated command prompt and run
sc qc diagtrack

In my case the service was running without errors
2. From the Windows 10 device, verify the on-boarding script ran successfully
Open the Application Event Log and look for Event ID 20

In my case the On-boarding script ran successfully
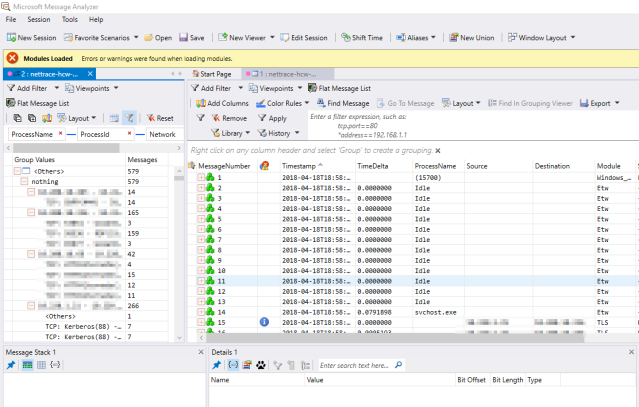
3. From the Windows 10 device, check the event logs for any on-boarding errors
Open the following event log and look for errors
- Microsoft>Windows>SENSE>Operational

In my case I could see HTTP errors relating to Windows Defender ATP URL’s
4. Next, run the WDATP Connectivity Analyzer tool to verify that your Windows 10 device can access the Windows Defender ATP URL’s
- Windows Defender ATP clients need access to these URL’s
- To verify access, download and extract the WDATP Connectivity Analyzer tool from here
Note about running the WDATP Connectivity Analyzer tool
The Widows Defender ATP sensor runs in system context using the LocalSystem account. Therefore, when running WDATP Connectivity Analyzer tool you need to run it in LocalSystem context. The Sysinternals utility “PSExec.exe” can be used to achieve this.
On your Windows 10 client, open a command prompt and browse to the extracted WDATP Connectivity Analyzer folder

Run the following command
Psexec.exe –I –s cmd.exe
This will open another command prompt under the load system context. You can verify this using “whoami”

From this new command prompt (under the local system context) browse to the WDATP Connectivity Analyzer folder and run WDATPConnectivityAnalyzer.cmd

Once complete, review the log file (WDATPConnectivityAnalyzer.txt) that was generated in the WDATP Connectivity Analyzer folder

In my case I could see “403” errors connecting to the Widows Defender ATP URL’s. I consulted with the networks team who could see the internet proxy blocking the connections. After the networks team created an exception for the URL’s I re-ran the connectivity tests. The WDATP Connectivity Analyzer log showed a “200” (success)

Soon after, my Windows 10 devices started to appear in the Machine List in the Windows Defender ATP portal